How to Identify and Prevent Phishing Attacks

Current Threat
Phishing attacks have become a common tactic used by hacker groups in recent years. Hackers impersonate a victim's colleague or organization through various channels, such as emails, instant messaging softwares, SMS messages, etc., to lure victims into divulging sensitive information such as login credentials, bank account numbers and transaction passwords. According to the 2022 Data Breach Investigations Report released by network operator Verizon, 75% of social engineering attacks in North America last year involved phishing, and over 33 million accounts were targeted by phishing attacks in just one year, with 82% of the violations involving human factors, largely representing employees who were tricked into clicking malicious links and logging into fraudulent websites.
Common Types of Phishing Attacks
1. Deceptive Phishing
Deceptive phishing is the most common type of phishing scam to date. Scammers impersonate legitimate companies in an attempt to steal personal data or login information. These emails often use threats or commands to create a sense of urgency, forcing users to act in accordance with the attacker's demands.

In these types of attacks, common techniques include:
• Adding legitimate links: Attackers add correct information about the organization (such as official website links) to the email to bypass security checks.
• Source code mixing: When creating a fake website login page, attackers usually mix malicious code with normal code to bypass Exchange Online Protection (EOP) detection.
• Shortened links: To avoid triggering security alerts, attackers usually generate shortened links for fake websites and apply them to phishing emails to bypass security email gateways (SEG) detection.
• Simplified email content: Attackers evade security checks by simplifying email content. For example, they may choose to send images with deceptive terms instead of plain text to carry out the attack.
2. Spear Phishing
Not all phishing attacks use the "casting a wide net" strategy. Spear phishing, which targets messages based on specific targets, often has better results. In this type of attack, scammers use the target's name, position, company, work phone number, and other information to tailor the attack email to make the recipient believe they have a connection with the sender. When the recipient clicks on a malicious URL or downloads an email attachment, hackers can easily obtain their personal data. Spear phishing is common on social media sites like LinkedIn and Twitter. Attackers can combine information from these sites with other data to create targeted attack emails.

In these types of attacks, common techniques include:
• Cloud service abuse: Attackers store malicious files on Dropbox, Box, Google Drive, and other cloud services. By default, IT personnel do not disable these services, and the organization's email filter does not mark malicious files.
• Collection of email metadata: Attackers need a lot of information to launch convincing spear phishing campaigns. A common method is to send emails to all employees and collect the metadata carried by the email server to understand the email address format used by internal employees.
• Social media message mining: When attackers want to understand the target company's employees, they usually use social media to learn about the organization's structure and members, and choose suitable targets for subsequent targeted attacks.
• Artificial intelligence abuse: With the maturity of artificial intelligence technology, it has opened the door for more and more phishing attacks, which can extract personal data from social media sites, create "deep fakes" videos, or tailor emails, making fraud easier.
3. Whaling
Spear phishers can target anyone in the organization, including executives. This is the meaning of "whaling," which is an evolved form of spear phishing that refers to phishing attacks targeting senior executives and other senior personnel within an organization. Attackers usually implement such attacks by making the email content personalized and specifically tailored to the relevant targets.
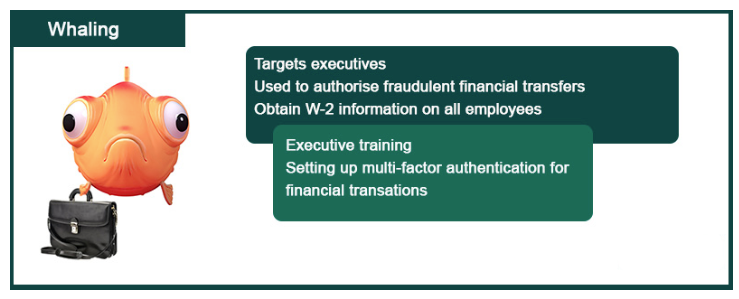
In these types of attacks, common techniques include:
• Penetration attacks: Attackers use malware to penetrate the target network and invade executive accounts.
• Follow-up via phone: Attackers confirm the authenticity of emails through phone calls, and this social engineering strategy helps alleviate the target's suspicion.
• Supply chain information: Attackers use supplier information to deceive victims into thinking that the email appears to come from a trusted partner.
4. Pharming
As users become increasingly aware of traditional phishing scams, some attackers have abandoned the idea of "luring" victims. Instead, they use deception techniques such as man-in-the-middle attacks and DNS cache poisoning. Even if the victim enters the correct domain name, the attacker can redirect them to their designated malicious website.
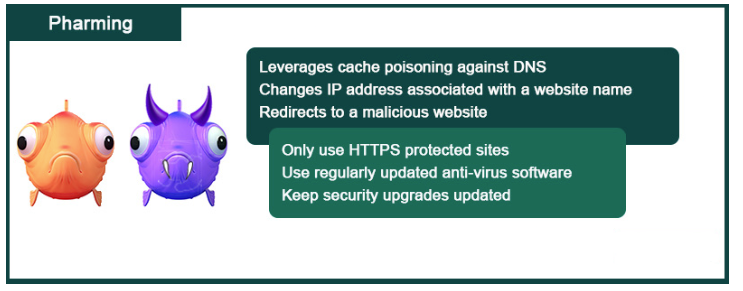
In these types of attacks, common techniques include:
• Malware: Attackers send emails containing malware that modifies files on the recipient's computer. After the host files are modified, all URLs are redirected to a website controlled by the attacker, making it easier to install malware or steal information from the victim.
• DNS cache poisoning: Attackers may choose to skip individual users' computers and directly attack DNS servers to modify mapping records, potentially compromising URL requests for millions of network users.
5. Identification and Prevention
• Review email subject lines
Be wary of suspicious email subject lines. Phishing emails from hacker organizations usually cover keywords such as "work reports," "business training," "attendance lists," "personal income tax reform," "salary adjustments," and so on. If you receive an email containing similar keywords, be cautious about clicking on it.
• Review sender addresses
Attackers often use email addresses that are highly similar to those of the impersonated party (missing domain name characters/ replacement/ exchange order, etc.). After receiving the email, ensure that the sender's address matches the actual email address of the organization or individual, and remain vigilant against personal email addresses or addresses with unusual spellings.
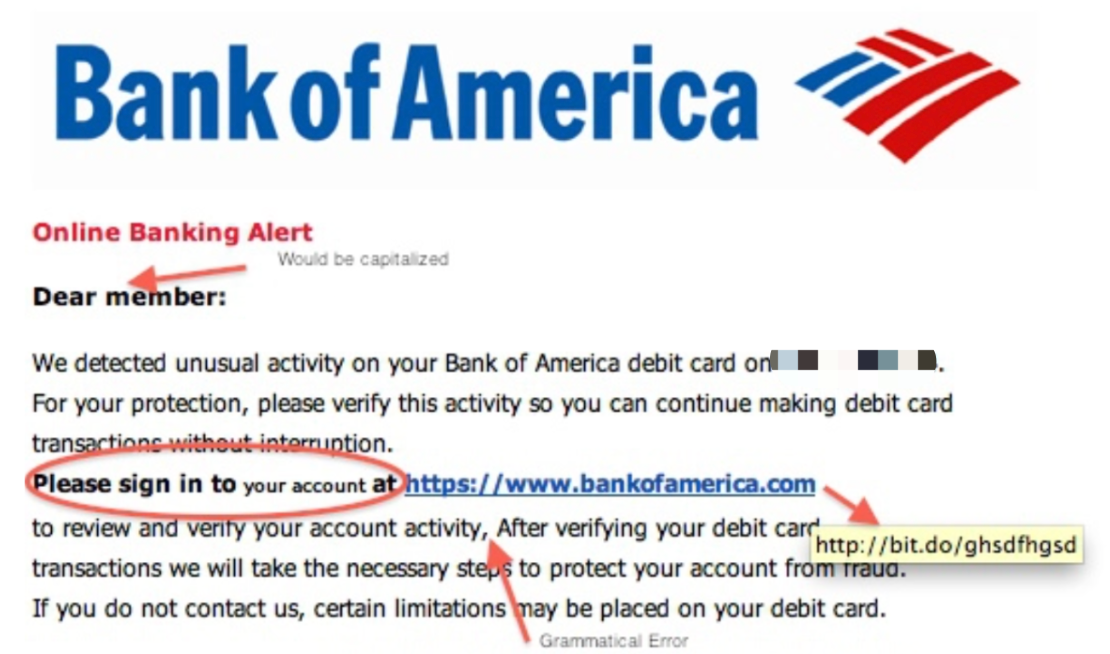
• Review email content
Check whether there are syntax or spelling errors in the email content, pay attention to details such as the sender's avatar, name, wording, closing and be cautious when clicking on links in the email, especially short links or link buttons in the body of the email. Check whether there is any inconsistency between the text and the link, for example, the "unsubscribe" function in some spam email bodies, the link may be a malicious program download address.
• Analyze the purpose of the email content
Be cautious of emails that use generic greetings such as "Dear User" or "Dear Colleague," or intentionally create a sense of urgency with statements such as "account abnormality" or "please reply urgently." If you receive an email requesting login credentials, use other channels to verify and confirm before sending it through an encrypted channel.
Pay attention to email warning messages
Gmail's security mechanism can detect and warn of some suspicious emails. After receiving such emails, do not click on any links or download attachments, and promptly verify the safety of the email with the sender.
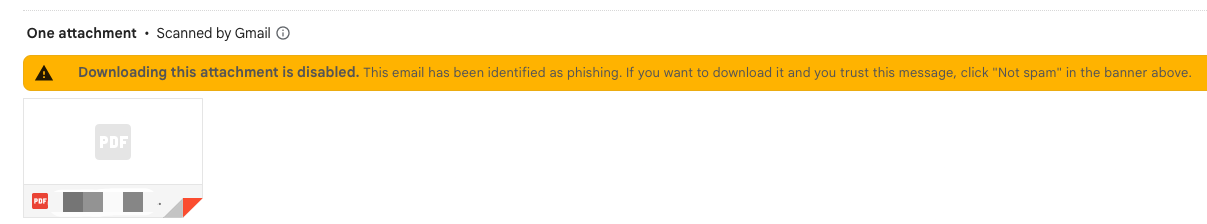
Pay attention to email sending time
Hackers often choose to launch phishing attacks on Mondays or Fridays, as there is more communication between corporate employees and external organizations during these two time periods, making it easier to become a victim. Be especially cautious with emails received during these time periods.
Security Recommendations
1. Pay attention to personal information security. Do not disclose important information such as phone numbers, email addresses, and job content on social media platforms. When shopping online, use pseudonyms as much as possible and set up virtual phone numbers. After receiving the order information, promptly clean up the information to avoid targeted attacks by hackers.
2. Develop a good password awareness. Use different passwords for different accounts, set high-strength passwords, and enable 2FA authentication, and regularly change passwords.
3. If the email involves operations such as requiring login credentials, permission applications, and fund transactions, it is necessary to verify again with the sender through channels such as phone calls, WeChat, WhatsApp and Slack.
4. Before accessing a URL, check whether the site is open with HTTPS, and carefully check whether the URL will be redirected to an unknown/suspicious website.
5. It is recommended to use the Chrome browser and upgrade it in a timely manner. Immediately stop visiting dangerous websites prompted by the browser, and do not enter personal information on unfamiliar websites.
6. Use official and legitimate channels to download required software and upgrade software/systems in a timely manner.
7. Be vigilant on all communication platforms. Attackers no longer only use email for phishing attacks, and there will be more and more phishing activities conducted through different channels.

